Trezor Login: Safeguard Your Crypto Future with Confidence
Explore how Trezor Login redefines crypto security through offline authentication, hardware verification, and total ownership of your digital wealth.
Introduction
Cryptocurrency is a revolution in finance — but with innovation comes the need for protection. Trezor Login provides the highest level of security for accessing and managing digital assets. Instead of trusting centralized platforms, users gain control over their crypto through hardware-based verification, ensuring their private keys never leave their devices.
For investors and traders alike, this login process is the gateway to peace of mind — blending convenience with cutting-edge cryptography.
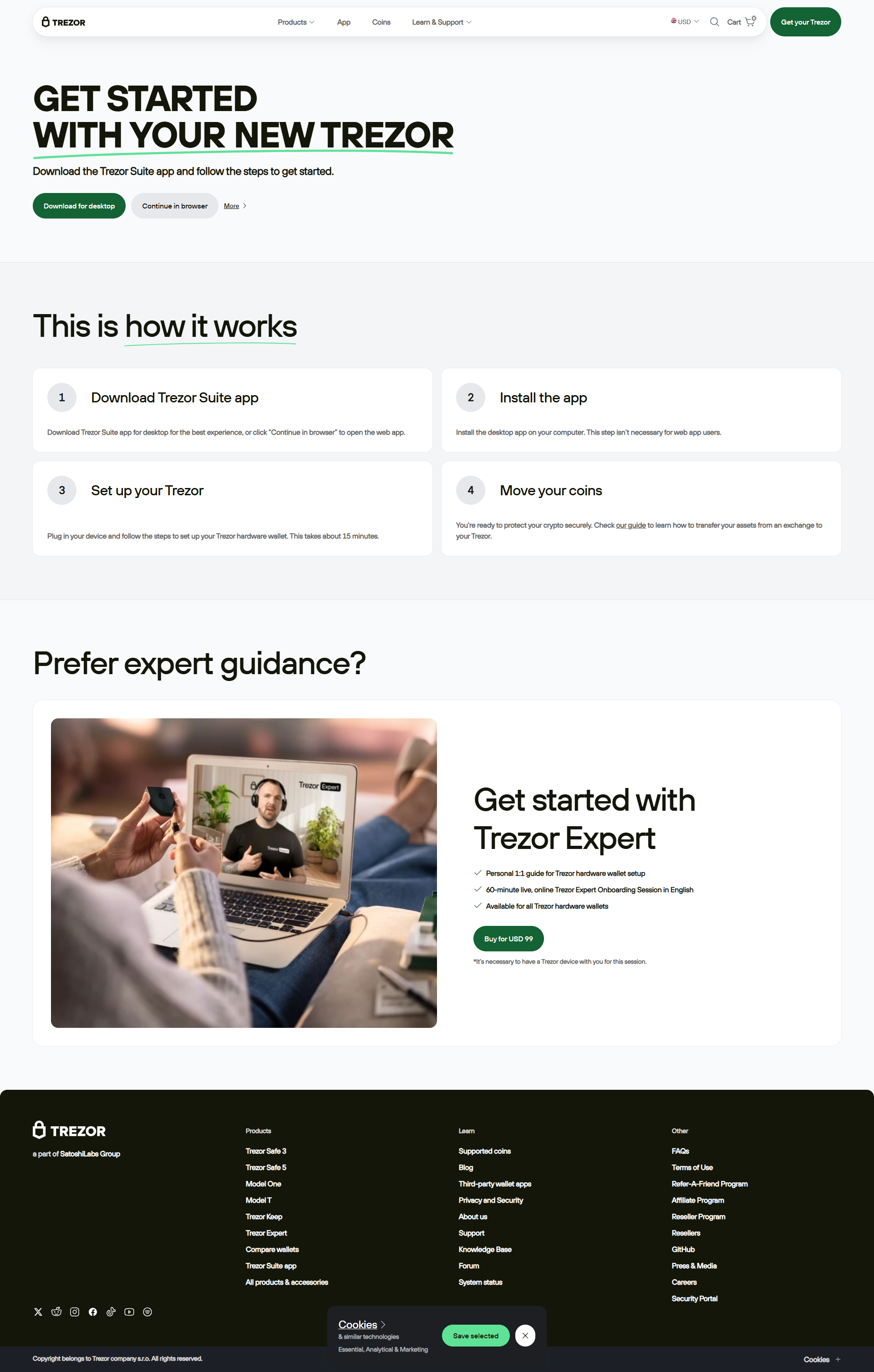
How Trezor Login Works
- Connect Your Trezor: Attach your Trezor hardware wallet via USB or OTG cable.
- Open Trezor Suite or Website: Access your wallet interface through Trezor.io.
- Authenticate: Confirm login actions directly on the device’s secure screen.
- Access Your Assets: Manage your cryptocurrencies safely and efficiently.
Every login step is completed locally — your private key never touches the internet, eliminating common attack vectors like phishing or malware injection.
Top Benefits of Trezor Login
🔒 Complete Offline Security
Your private keys stay inside the Trezor device — safe from hackers and data leaks.
🧠 User-Friendly Experience
Simple device prompts make login intuitive even for beginners in crypto.
🛡️ Phishing Resistance
Every login request is verified on-screen, preventing fraudulent impersonation.
🌍 Global Accessibility
Compatible with desktop, browser, and supported third-party wallet integrations.
Trezor Login vs. Software Wallet Logins
| Feature | Trezor Login | Software Wallet Login |
|---|---|---|
| Private Key Storage | Offline on device | Online or local files |
| Phishing Protection | Hardware verification | Dependent on software integrity |
| Ease of Use | Plug-and-confirm simplicity | Manual sign-ins required |
| Security Level | High – hardware isolated | Moderate – software dependent |
Common Problems and Solutions
Problem: Device not detected
Fix: Try using a different USB cable or port, and make sure the Trezor Bridge is installed.
Problem: Login request not appearing
Fix: Reboot your device and refresh the Trezor Suite interface.
Problem: Browser not supported
Fix: Use Chrome, Firefox, or Brave for best compatibility.
FAQs About Trezor Login
Q1: Can I use Trezor Login without internet?
A: You need internet only for interface access. The private keys never go online.
Q2: Is Trezor Login safe for beginners?
A: Absolutely — the design ensures ease of use and zero technical barriers.
Q3: What happens if I lose my Trezor?
A: Simply restore your funds using the recovery seed provided during setup.
Experience the Future of Crypto Security
With Trezor Login, you hold the keys to your digital freedom. Stay protected, stay independent, and let your crypto work safely for you.